Heartbleed
 Heartbleed also known as CVE-2014-0160 is a vulnerability in OpenSSL heartbeat implementation. It's not a flaw in TLS/SSL, however it can lead to
potential issues since with this vulnerability a hacker can see parts of the server's memory. For more information on heartbleed you can visit heartbleed.com or this very good
guide.
Heartbleed also known as CVE-2014-0160 is a vulnerability in OpenSSL heartbeat implementation. It's not a flaw in TLS/SSL, however it can lead to
potential issues since with this vulnerability a hacker can see parts of the server's memory. For more information on heartbleed you can visit heartbleed.com or this very good
guide.
The first step
The first step is to identify if your server has OpenSSL and if yes you should immediately patch it up. Most of the Apache / Ngix and Linux distros by now have released fixes for the heartbleed bug by now. You can also check if a server is compromised using the following website http://filippo.io/Heartbleed
Has your server been compromised?
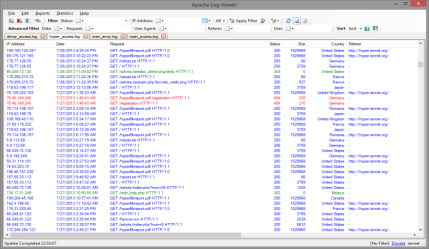
Once patched the second question to ask is if your server or your users/visitors have been compromised. Here comes the log analytics. Once that you system is fully patched it is time to understand if somebody did really try to hack your visitors or gain access to your servers.
This to try out:
- Check to see if any POSTs requests are being requested without requesting the previous html pages. This could be an indication that hackers have accessed cookies and are trying to impersonate your users.
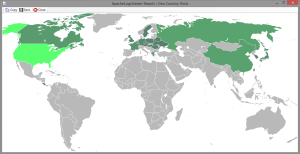
- Check the visitors countries see if there are any unusual visitors from any strange country
- See for any spikes in errors 500 on the server.
- Identify any access from a particular IP address which could be hitting your website within the same time period.
- Identify User-Agents and see for any malicious strings
- Observe requests for any particular resources. Check that they are not targeting any particular location within your website.
There is a lot of analysis you can do on the log file. And the above is just a simple suggestion. In many cases the media have blown out of proportion the issue and being ale to extract a particular private key is highly unlikely since you would require to get the full certificate and be able to compile it correctly. However it should be possible to be able to steal cookies and impersonate users. Stealing passwords is also possible. Having said this, the issue is not to be taken lightly and all website owners must ensure that your website has not been compromised. All major websites are requesting certificates to be regenerated, so it might be safe to just do so.